on
XSRF (CSRF) Protection - Double Submit Cookie
Introduction
If storing the CSRF token in session (Synchronizer Token) is problematic when the user base is pretty large, an alternative defense is use of a double submit cookie. A double submit cookie is defined as sending a pseudo-random value in both a cookie (header) and as a request parameter, where the server verifies if the cookie value and request value match.
How?
When a user authenticates to a site, the site generates a pseudo-random value and set it as a cookie on the user's machine.
[caption id="attachment_446" align="aligncenter" width="716"]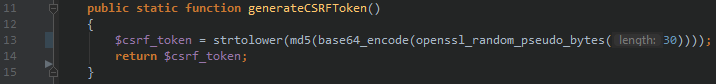 Generate a pseudo-random string using the mod_ssl for php_apache[/caption]
Generate a pseudo-random string using the mod_ssl for php_apache[/caption]
[caption id="attachment_442" align="aligncenter" width="612"]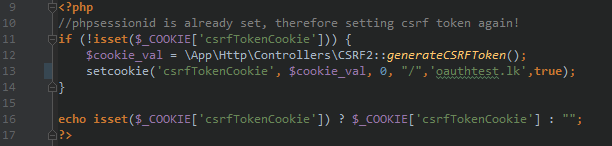 Setting "csrfTokenCookie" in the user's browser[/caption]
Setting "csrfTokenCookie" in the user's browser[/caption]
The site then requires that every transaction request include this random value as a hidden form value.
[caption id="attachment_443" align="aligncenter" width="808"]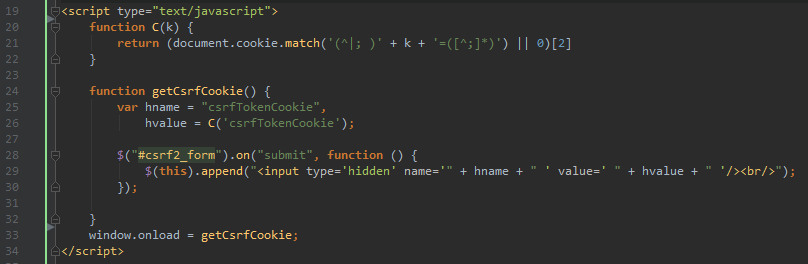 Appending a hidden input field in the form body via JavaScript at submit time[/caption]
Appending a hidden input field in the form body via JavaScript at submit time[/caption]
The server will then verify the header cookie value with the request csrf_token value upon submission.
[caption id="attachment_444" align="aligncenter" width="1118"]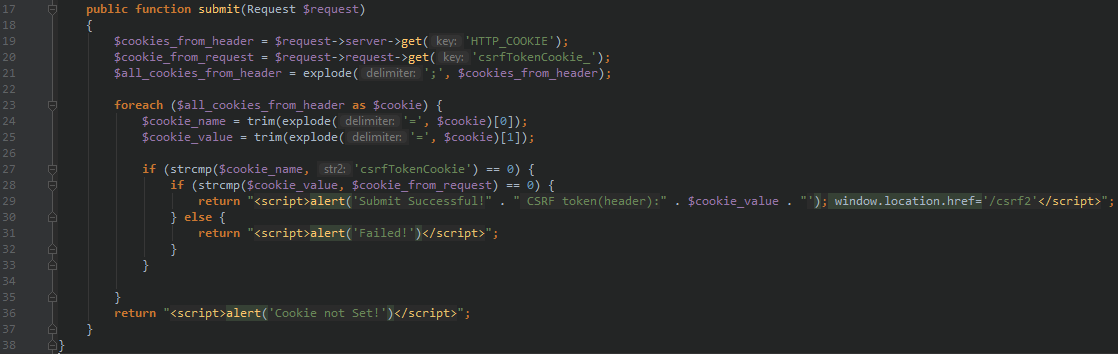 Extracting Header and Body details from the POST request and getting both CSRF token values for comparison[/caption]
Extracting Header and Body details from the POST request and getting both CSRF token values for comparison[/caption]
A cross origin attacker cannot read any data sent from the server or modify cookie values, because of the same-origin policy. This means that while an attacker can force a victim to send any value he wants with a malicious CSRF request, the attacker will be unable to modify or read the value stored in the cookie.
[caption id="attachment_447" align="aligncenter" width="441"]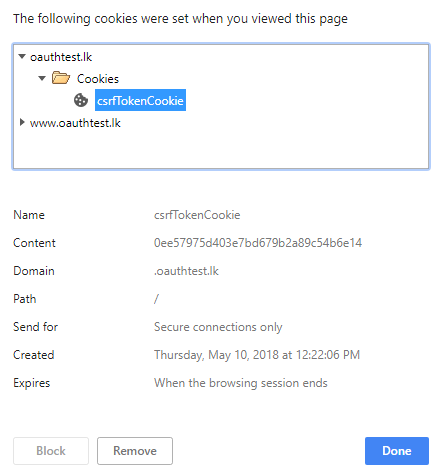 CSRF token (Over Secure connections)[/caption]
CSRF token (Over Secure connections)[/caption]
Demo
[caption id="attachment_448" align="aligncenter" width="346"] Form[/caption]
Form[/caption]
[caption id="attachment_449" align="aligncenter" width="461"]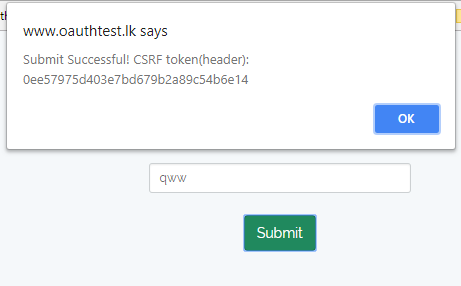 Successful token validation[/caption]
Successful token validation[/caption]
To demonstrate a Token Falsification, we can statically edit the request CSRF_token value to a invalid token string.
[caption id="attachment_450" align="aligncenter" width="761"]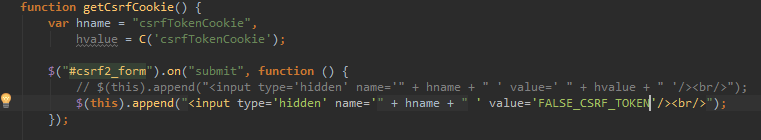 Set request token value to an invalid string[/caption]
Set request token value to an invalid string[/caption]
The validation fails with the invalid request_token_string.
[caption id="attachment_451" align="aligncenter" width="465"]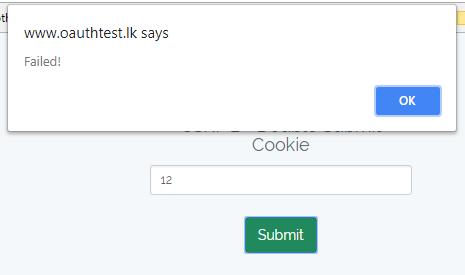 Validation fails[/caption]
Validation fails[/caption]
Conclusion
Since the cookie value and the request parameter or form value must be the same, the attacker will be unable to successfully force the submission of a request with the random CSRF value.